2nd puc computer science model question papers with answers,2nd puc computer science solved model question papers
PU-II COMPUTER SCIENCE
SOLVED MODEL QUESTION PAPER 2
Answer all the
questions.
Each question carries 1 mark. (10 X 1 = 10)
Each question carries 1 mark. (10 X 1 = 10)
1. Expand the term ISA.
Ans: Industry Standard Architecture.
2. Draw XNOR gate.
Ans:
3. What is traversing?
Ans: the process of accessing each
data item exactly once to perform some operation is called traversing
4. Write the significance of scope resolution
operator.
Ans: scope resolution operator is used to define the member function
outside the class definition.
5. List the operators used with the pointers.
Ans: indirection operator (*) and address of operator (&).
6. What is data warehouse?
Ans: a data warehouse is a repository of an organization’s
electronically stored data.
7. Expand the term ARPANET.
Ans: Advanced Research Projects Agency NETwork.
8. What is virus?
Ans: computer virus is a malicious program that
requires a host and is designed to make a system sick.
9. Name any two web browsers.
Ans: internet explorer, firefox Mozilla, google chrome, netscape
navigator, opera mini etc.
10. What is web hosting?
Ans: web hosting is a business of providing storage
space and access for websites.
Answer any five of
the following. Each question carry 2 marks (5
X 2 = 10)
11. State and prove indempotence law.
Ans: this law states that when a variable is combines with itself
using OR or AND operator, the output is the same variable.
Proof: a) X+X=X
If X=0, consider LHS=X+X
=0+0
=0
=X
=RHS
If X=1, consider LHS=X+X
=1+1
=1
=x
=RHS
b)
X.X=X
If X=0, consider LHS=XX
=0.0
=0
=X
=RHS
If X=1, consider LHS=X.X
=1.1
=1
=X
=RHS
12. Show that X(X+Y)=X
Ans: LHS= X(X+Y)
=X.X+X.Y
=X+XY
=X(1+Y)
=X.1
=X
=RHS
13. What is inheritance?
Ans: inheritance is a process of
acquiring properties from parent class to child class
14. Name any two types of constructors.
Ans: default constructor, parameterized constructor, copy
constructor.
15. Explain getline() function with an example.
Ans: getline() function is used to read a whole line of text.
Ex: char book[SIZE];
fstream fin;
fin.getline(book,SIZE);
16. Name the database users.
Ans: - application programmers and system analysts
-
- End users
- - Database administrator(DBA)
-
- Database designers
17. Write the syntax of UPDATE command with an
example.
Ans: syntax: update table_name set column1=value1,column2=value2…column=valueN
where[condition];
Ex: update employee set address=’gadag’ where empid=1;
18. What is the need of networking?
Ans: - file sharing
-
Print sharing
-
Email tools for communication
-
Remote access
-
Sharing database to multiple users.
Answer any five of
the following.
Each question carries 3 marks. (5 X 3 = 15)
Each question carries 3 marks. (5 X 3 = 15)
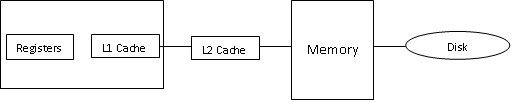
19. What is cache memory? Explain its types.
Ans: The cache memory is a very high speed memory
placed in between RAM and CPU. Cache memory stores data that is used more often,
temporarily and makes it available to CPU at a fast rate. During processing,
the CPU first checks cache for the required data. If data is not found in
cache, then it looks in the RAM for data
Cache memory is very
expensive, so it is smaller in size. Computers have cache memory of sizes 256
KB to 2 MB
Cache memory is built into
the processor and may also be located next to it on a separate chip between CPU
and RAM. Cache built into CPU is faster than separate cache almost at the speed
of the microprocessor itself. However separate cache is roughly twice as fast
as RAM. The CPU has a built –in level 1(L1) cache and level2 (L2) cache high
end processor nowadays comes with built-in L3 cache, processor like Intel Core
i7
20. Explain XOR gate with diagram and truth
table.
Ans: XOR gate produces output 1 for only those input combinations that have odd number of 1's.
21. Write any three features of array.
Ans: -array size should be positive number only.
-
- String array always terminates with null
character (‘\0’).
-
- Array elements are counted from 0 to n-1.
-
- Useful for multiple reading of elements.
22. Differentiate between static and dynamic
allocation of memory.
Ans:
Static Memory allocation
|
Dynamic Memory allocation
|
-
The amount of memory to be allocated is predicted and pre known
|
-
The amount of memory to be allocated is not known
|
-
It is allocated during compilation
|
-
It is allocated during run-time
|
-
All the variables declared normally, are allocated memory
statically
Ex:
int a;
|
-
Allocation and de-allocation of objects using the new and delete
operators
|
23. Differentiate between read() and write()
functions.
Ans:
read()
|
write()
|
1.
The
read() member function belongs to
ifstream class.
|
1. The
write() member function belongs to ofstream class.
|
2.
Syntax:
fin.read((char*)&variable,sizeof(variable));
|
2. Syntax:
fout.write((char*)&variable,sizeof(variable));
|
3.
Ex:
student s;
ifstream fin(“text.txt”,ios::binary);
fin.read((char *)&s,sizeof(s));
|
3. Ex:
student s;
ofstream fout(“text.txt”,ios::binary);
fout.write((char *)&s,sizeof(s));
|
24. Explain three level RDBMS architecture.
Ans: it is a three levels of
architecture namely, internal, conceptual and external levels.
Internal level: internal level is the
lowest level of data abstraction that deals with the physical representation of
the database on the computer and thus, is known as physical level. It describes
how the data is physically stored and organized on the storage medium. It
includes storage space allocation techniques for data and indexes, data
compression and encryption techniques, and record placement
Conceptual level: conceptual level describes
what data is stored in the database, the relationships among the data and
complete view of the user’s requirements without any concern for the physical
implementation. i.e. it hides the complexity of physical storage structures.
External level: this level permits the
user to access data in a way that is customized according to their needs, so
that the same data can be seen by different users in different ways at the same
time. In this way, it provides a powerful and flexible security mechanism by
hiding the parts of the database from certain users, as the user is not aware
of existence of any attributes that are missing from the view
25. What is shareware software? Mention its
limitations.
Ans: software made
available with the right to redistribute copies, but it is stipulated that if
one intends to use the software, often after a certain period of time, then a
license fee should be paid.Limitations of shareware:
i) In shareware the source code is not available.
ii) Modifications to the software are not allowed.
26. Name any three formatting tags in HTML.
Ans: <B> is used to make text Bold.<U> is used to draw underline.
<I> is used to make text italics.
Answer any seven of
the following. Each carries 5 marks (7
X 5 = 35)
27. Using K-map, simplify the following
expressions in four variables W,X,Y and Z.
m0,m2,m4,m8,m9,m10,m11,m12,m13.
28. Write an algorithm to illustrate enqueue.
Ans: Step 1: if REAR=N then
PRINT “overflow”
Exit
Step 2: if FRONT=NULL then
Step 2: if FRONT=NULL then
FRONT=0
REAR=0
else
REAR=REAR+1
Step 3:
QUEUE[REAR]=ITEM
Step 4: return
29. Illustrate an algorithm to delete an
element from a stack.
Ans: An algorithm for POP() OperationStep 1: if TOP=0 then
PRINT “Stack is empty”
Exit
Step 2: ITEM=STACK[TOP]
Step 2: ITEM=STACK[TOP]
Step 3: TOP=TOP-1
30. Write the applications of OOP.
Ans: Applications of OOP are as follows- Computer graphic applications
- CAD/CAM software
- Object oriented database
- User interface design such as windows
- Real-time systems
- Simulation and modeling
- Artificial intelligence and expert systems
31. Explain defining a function outside the class
definition with an example.
Ans: To define member function inside a
class the function declaration within the class is replaced by actual function
definition inside the class. Only small functions are defined inside class
definition.Ex:
class room
{
int length;
int breadth;
public: void getdata()
{
cin>>length;
cin>>breadth;
}
void putdata()
{
cout<<length;
cout<<breadth;
}
};
To define member
functions written outside the class definition replaced by actual function
definition outside the class.
Ex:
class room
{
int length;
int breadth;
public: void getdata();
void putdata();
};
void room::getdata()
{
cin>>length;
cin>>breadth;
Ex:
class room
{
int length;
int breadth;
public: void getdata();
void putdata();
};
void room::getdata()
{
cin>>length;
cin>>breadth;
}
void
room::putdata()
{
cout<<length;
cout<<breadth;
}
{
cout<<length;
cout<<breadth;
}
The symbol :: is known as scope resolution operator. The scope
resolution operator identifies the function as a member of particular class.
The use of scope resolution operator implies that these member functions are
defined outside the class
32. Write the advantages of inline functions.
Ans: - the inline member functions are compact function calls.- Therefore the size of the object code is considerably reduced.
- The speed of execution of a program increases.
- Very efficient code can be generated.
- The readability of the program increases.
33. What is destructor? Explain with its syntax
and definition.
Ans: A destructor is a special member
function that will be executed automatically when an object is destroyed. It
will have, like constructor, the same name as that of the class but preceded by
a tilde (~).A destructor will be called automatically when an object is destroyed. Destroying an object means de-allocating all the resources such as memory that was allocated for the object by the constructor.
Syntax:
class class_name
{
private: data_variables;
public: class_name() //constructor
~class_name() //destructor
};
Ex:
#include<iostream.h>
#include<conio.h>
class num
{
int x;
public:
num();
void display();
~num();
};
num::num()
{
cout<<”In constructor:\n”;
x=100;
}
num::~num()
{
cout<<”In desctructor:\n”;
}
void num::display()
{
cout<<”Value of x=”<<x;
}
void main()
{
num n;
n.display();
getch();
}
34. Describe the types of inheritance with
examples.
Ans: following are the types of
inheritance- Single inheritance: if a class is derived from a single base class, it is called as single inheritance
- Multilevel inheritance: the classes can also be derived from the classes that are already
derived. This type of inheritance is called multilevel inheritance.
- Multiple
inheritance: if a class is derived from more than one base class, it is
known as
multiple inheritance
- Hierarchical inheritance: if a number of classes are derived from a single
base class, it is called as
hierarchical inheritance
hierarchical inheritance
- Hybrid inheritance: it is a combination of Hierarchical and Multiple inheritance.
35. Explain the features of database system.
Ans: in the database approach, the data
is stored at a central location and is shared among multiple users. Thus, the
main advantage of DBMS is centralized data management. The advantages of
centralized database system are as follows:- Controlled data redundancy: elimination of duplication of data item in different files ensures consistency and saves the storage space. The redundancy in the database cannot be eliminated completely as there could be some performance and technical reasons for having some amount of redundancy.
- Enforcing data integrity: data integrity refers to the validity of data and it can be compromised in a number of ways.
- Data sharing: the data stored in the database can be shared among multiple users or application programs. It is possible to satisfy the data requirements of the new applications without creating any additional data or with minimal modification
- Ease of application development: the application programmer needs to develop the application programs according to user’s needs. The other issues like concurrent access, security, data integrity etc are handled by the RDBMS itself
- Data security: since the data is stored centrally data security checks can be carried out whenever access is attempted to sensitive data. To ensure security, a RDBMS provides security tools such as used codes and passwords. Different checks can be established for each type of access like addition, modification, deletion etc to each piece of information in the database
- Multiple user interfaces: For various users having different technical knowledge DBMS provides different types of interfaces such as query languages, application program interfaces, and graphical user interfaces (GUI)
- Backup and recovery: RDBMS provides backup and recovery subsystem that is responsible for recovery from hardware and software failures. For example, if the failure occurs in between the transaction, the RDBMS recovery subsystem either reverts back the database to the state to the previous state of the transaction or resumes the transaction from the point it was interrupted so that its complete effect can be recorded in the database
36. Describe any five logical operators with an
example.
Ans: ALL: This operator is used
to compare a value to all values in another value set.AND: This operator allows the existence of multiple conditions in an SQL statements’ WHERE clause.
EXISTS: This operator is used to search for the presence of a row in a specified table that meets certain criteria.
LIKE: This operator is used to compare a value to similar values using wildcard operators
IS NULL: This operator is used to compare a value with a NULL value.
37. Explain any five network topologies.
Ans: Bus
topology or linear topology: this consists of a single length of the
transmission medium onto which the various nodes are attached. The transmission
from any station travels the length of the bus, in both directions, and can be
received by all other stations. The bus has terminators at either end which absorb
the signal, removing it from the bus
-
Ring
topology or circular topology: In this topology each node is connected to
two and only two neighboring nodes and is transmitted to another. Thus data
travels in one direction only, from node to node around the ring. After passing
through each node, it returns to the sending node, which removes it
-
Star
topology: this topology consists of a central node to which all other nodes
are connected by a single path.
In star topology,
every node (computer workstation or any other peripheral) is connected to a
central node called a hub or switch. The switch is the server and the
peripherals are the clients.
Advantages
- ·Star networks are very reliable because if one computer or its connection breaks it doesn’t affect the other computers and their connections
Disadvantages
- An expensive network layout to install because of the amount of cables needed
- If the server crashes or stops working then no computers will be able to access the network
-
Tree
topology: In telecommunication networks, a tree network is a combination of
two or more star networks connected together. Each star network is a local area
network (LAN) in which there is a central computer or server to which all the workstation
nodes are directly linked. The central computers of the star networks are
connected to a main cable called the bus. Thus, a tree network is a bus network
of star networks.
- Mesh topology: A mesh network is a network topology in
which each node relays data for the network. All mesh nodes cooperate in the
distribution of data in the network.
The Mesh topology is commonly used in large internetworking
environments with stars, rings and buses attached to each node.
2nd puc computer science model 2 question papers and answers
 Reviewed by Vision Academy
on
January 14, 2020
Rating:
Reviewed by Vision Academy
on
January 14, 2020
Rating:
 Reviewed by Vision Academy
on
January 14, 2020
Rating:
Reviewed by Vision Academy
on
January 14, 2020
Rating:
















No comments: